Netjacking for Complete Idiots
by Dark Overlord of the DoC
The latest big thing in hacking these days is wireless 802.11 networking. The reason for this is that the hardware is cheap and open networks are abundant.
Wireless networks are popping up all over the place from corporate offices to trade shows, conference halls, libraries, coffee shops, parks, and personal residences.
In the corporate environment the majority of Wireless LANs (WLANs) are connected to the internal backbone of the company Intranet behind their corporate firewall, thus unknowingly giving everyone within a two-block radius full unrestricted access to the internal network and attached company resources.
Not all networks are private networks - there are many that are intended to be accessible to the public to attract business.
For example, there are many coffee shops that are offering free Internet access in hopes that people will spend more time drinking coffee at their establishment. Hotels are providing wireless access as a perk to attract guests, which is also cheaper then wiring all the rooms with Cat 5 for 100 MB Ethernet.
In Seattle, San Francisco, and other areas, there are groups and organizations that are setting up WLANs for free use in their neighborhood in a philanthropic manner.
What is Wi-Fi/802.11?
802.11 is a standard for WLANs developed by the Institute of Electrical and Electronics Engineers (IEEE). The standard deals with network association, data transfer, authentication, and privacy.
802.11 is the first draft of the protocol specifying transmission speeds of one and two megabits a second. The 802.11b specification describes a later update to the protocol for eleven megabit rates. (802.11a is a specification for 51 megabit rates but is not ready for prime time.)
The 802.11 WLAN protocol specifies the lowest-layer of the OSI network model (physical) from which other protocols such as TCP/IP, IPX, NetBEUI, etc. are built on.
On a traditional copper network, physical connectivity defines the network (discounting the use of Layer-2 switches and VLANs). Thus, security of these networks is primarily a physical exercise whereas with WLANs there are no physical constraints to connectivity.
Instead, the way networks are differentiated is through names called SSIDs. To connect to a particular network, all you need is the network name and to be within radio range of the wireless bridge. The SSID was never meant to provide real security but sadly that is how it is commonly being used in current deployments.
The 802.11 protocol supports Layer-3 encryption method called Wired Equivalent Privacy (WEP). WEP is a simple algorithm based on RSA's RC4 hashing scheme. Recent analysis has shown WEP encryption to be inadequate. The details of WEP and its weaknesses are beyond the scope of this text and will be the topic of a future article.
Hardware
For around $80 to $150 you can get a good PCMCIA card. I have seen older cards on eBay.com and OnSale.com for as little as $15. With this card and a standard laptop you can be walking down the street or sitting in the park with free Internet access. I recommend the Lucent cards for their features: external antenna options and cross-platform support.
If you plan on sniffing 802.11 frames, I suggest a card based on the PRISM chipset.
Software
All popular operating systems have the driver support for the more popular cards (Lucent/ORiNOCO, Cisco Aironet, BayStack, etc.). For the examples used in this document we will use Microsoft Windows since it is the easiest to set up and install.
Locating a WLAN
Locating a network is easy once you get the hang of it. For simplicity I will explain how to do this under Windows with a Lucent/ORiNOCO card and software.
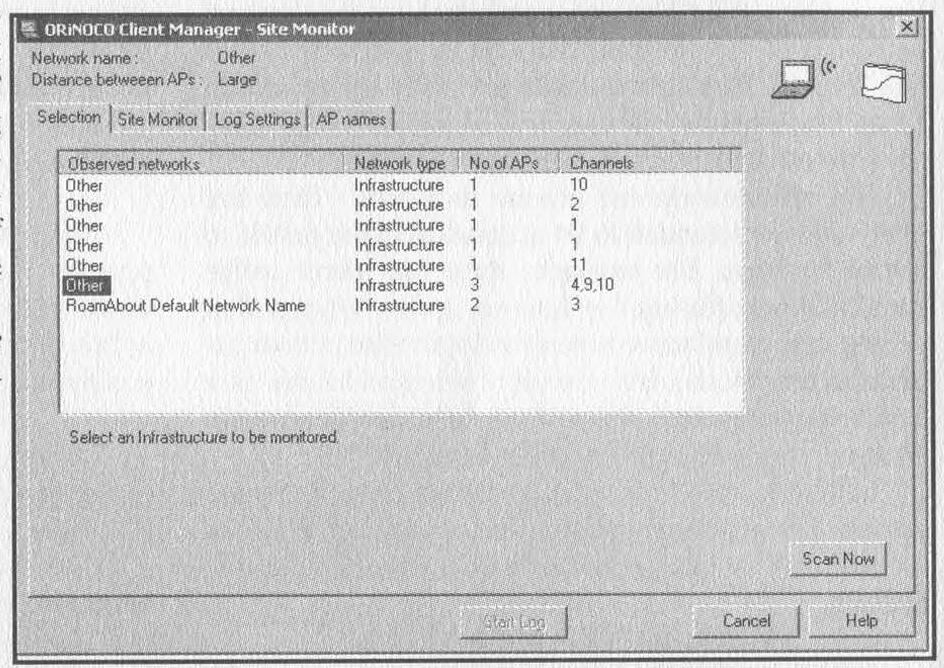
Once you have your card installed, run the ORiNOCO Client Manager software and set your SSID to ANY. From the Advanced menu of Client Manager select Site Monitor. A window should open listing all the local WLANs that are available from where you are standing. I recommend doing this first near a known network, then as you move around click on the Scan Now button to refresh the view (see Figure 1 for an example output taken on Market Street in San Francisco).
If you do not have a Lucent/ORiNOCO card you can manually search for common SSIDs. All cards come with an application to quickly change the SSID you are using. Simply program in the five or ten most common SSIDs (see below for a list of common SSIDs) and cycle though them, or just walk around until you get a link.
A more effective method is to sniff the 802.11 frames and look for beacons. This will require specialized software. Again, this is beyond the scope of this introductory text and will be the topic of a future article.
What Now?
At this point you can run WINIPCFG.EXE to get a DHCP lease on an IP.
After you get an IP address, you are on their network. You will be able to access the Internet (relatively anonymously). When you get on, click Network Neighborhood. You should be able to see the other hosts and shared resources available on that network (remember - if you can see them, they can see you).
If you have a sniffer such as NetXRay or dSniff installed on your system, you will be able to see packets sent to other wireless hosts and broadcast packets.
Whose Net Is It?
If you have a Yagi antenna (2.4 GHz) hooked up to your card you can use it to directionally find and help identify the owner of the WLAN.
High-gain (dB) Yagi antennas also are useful for surprisingly long-range connections. Distances as far as five to ten miles are possible.
From the DHCP lease you should get a domain name with which you can look up their domain registration or the company home page to find the address and location of the WLAN. Another method is looking up the owner of the IP address block in the ARIN database or tracerouting the IP address.
Is This Illegal?
If it isn't, it will be soon.
Walking around noting the location of WLANs that are out there is a gray-area thing since the people you are detecting are willingly transmitting beacons announcing their presence.
The act of requesting an IP address via DHCP and/or actively sniffing their LANs is clearly a violation of electronic trespassing laws and the Electronic Communications Privacy Act. You should do this type of experimentation only on your own private networks.
See Also
- Bay Area Wireless Users Group: www.bawug.org
- Surf and Sip Coffee Shop Internet Access: www.surfandsip.com
- www.wi2600.org/mediawhore/nf0/wireless
- IEEE 802.11 Standardization Group: grouper.ieee.org/groups/802/11
Most Common SSIDs
- tsunami
- AirWave
- WaveLAN Network
- WLAN
- linksys
- default
- TEKLOGIX
Shout Outs: Bill Paul, author of the FreeBSD Lucent card driver; Phillip "Edward" Nunez, for his research efforts.