Inline Patching Aspacked Applications
Author: x-Bi0dESC
My Operating System: Windows 2000
Prerequisite knowledge: Some basic asm knowledge, some idea of the PE-format
(e.g. what the whole shamazzle about EP's and OEP's which I’ll vaguely discuss)
Tools Required: OllyDbg (for unpacking+inlining), Imprec (for fixing the Imports),
Stripper (optional for the lazy ones like me so we will be using it, learn how to fix imports some other time.. but for you people on win 9x/me, Stripper don’t work on them os’s therefore you gotta fix imports manually or find another tool that supports them… maybe Aspackdie which you can find at http://www.exetools.com in the unpackers section, or maybe even PE-Scan).
Where to get the tools:Ollydbg = http://home.t-online.de/home/Ollydbg/
Imprec = http://wave.prohosting.com/mackt/main.htm
Stripper = http://www.is.svitonline.com/syd/stripper.html
Intro: Ok let me explain a little what Inline patching is first then I will
get to what the advantages are and how its done.
The example I am going to demonstrate on is the famous Application
NOTEPAD. The one I have supplied is packed with Aspack 2.xx.
Aspack is a commercial packer coded by Alexey Solodovnikov, who is the author of the infamous asprotect.
A PE file (portable executable) can be compressed (packed) in many different ways
and also protected for many different reasons such as file size and stronger
protection. If you attempt to open the packed exe in a dissasembler of such
you will notice no string-data and only some imports... this is because
the exe isn't decrypted/decompressed if you attempt to do a dead-listing.
What is inlining:
Inline patching is a technique used on applications packed with some sort
of packer (whether it'd be commercial or not) to apply patches without
unpacking the exe, patching, and then repacking. Rather then this, we Unpack the exe,
locate which bytes we need to patch, noting down the addresses and the bytes that need
patching, then patching the ORIGINALLY packed exe by making the exe overwrite certain bytes
during decompression (or rather before the exe jumps to it [O]riginal [E]entry [P]oint)
I suggest you read Mr_Geeks tutorial on unpacking aspack first then reading this
because we will be using the simple technique on locating the OEP in ollydbg discussed
in his tutorial.. (Get it from here: http://biw.rult.at/tuts/mupaspack.rar)
BEGINNING:
Ok guys another note for you newbie’s out there, if you haven't already gotten
PEiD (which is a great tool for identifying what exe's are compiled/packed with,
coded by some of the dudes from unpacking gods .. HI snaker =]) get it from
http://www.peid.has.it/
Ok so we know that this application provided (notepad.exe) is packed with
aspack 2.12… how? Well I packed it myself but PEiD does a brilliant job of telling you what it’s packed with, give it a shot ;).
Our objective is to remove the 32kb limit or remove the nag and make it automatically
open up WordPad instead of nagging us first. (By the way I had to get this version of Notepad off a win95 machine coz win2k version don’t have the limit :/)
So what do we do.. How do we crack a packed file!?
Better yet how do we compile those tiny patchers if it’s packed?
Easy.. :) well sorta.. I must warn you it takes a little longer to do because we will
manually coding the asm in via ollydbg.. I must say its not very appropriate
for if you need to do 15+ bytes of patching :/ but its up to you if you wanna spend
some time making a quality patch :).
Ok so I’ll do the lazy thing and unpack this app with Stripper because it takes like 5 seconds
to unpack the exe as opposed to like 1 minute ;) (I provided the unpacked file as well in the unpacked dir) but if you decide to do the manual way you can read Mr_geek's tute then fix the imports with Imprec (read another tute maybe one on upx.. its very similar or exactly the same).
Ok so fire up Stripper, select notepad.exe, click unpack, now it’s usually saved as
_notepad.exe ... this is the file we will be opening up in OllyDbg to examine.
Fire up ollydbg, you should have the CPU window, Breakpoints Window, And the Executable
Modules window open at least (read the tute on the n2c site on how to set up ollydbg http://n2c.no-ip.com/ ).
Now load the file into olly (File->open select where you stored file, choose _notepad.exe which
is the unpacked EXE)
SO we know that Notepad tells us that the file is too big to open in notepad if the file is greater then 32kb.. Try it out, you will see the Message: Error: This file is too large for Notepad to open. Would you like to use WordPad to read this file?Ok this looks like a MessageBox....
COOL now that we’ve got know what the error msg is we can try using ollydbg to point us to where the messagebox gets called from and why?
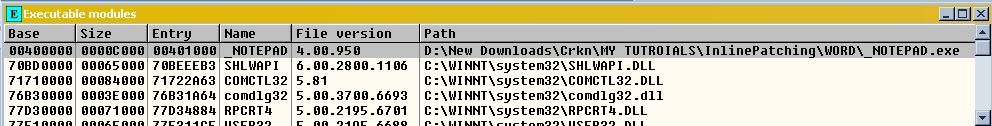
So we’re in olly, the UNPACKED FILE _notepad.exe is loaded, Now we Should have the executable modules window open:
So on the part that is highlighted in the picture, Right-Click and goto “View Names” or alternatively press ctrl+n.
Now a window should have popped up:
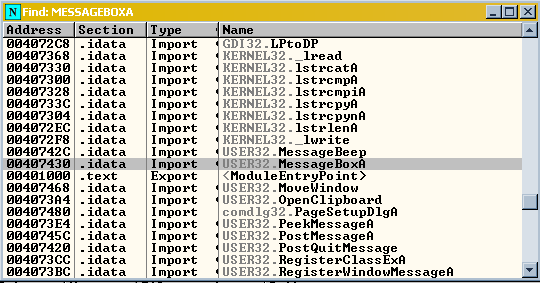
Now Because we know this is a MessageBox, then we will see if it uses the common api for a message box, “MessageBoxA”. So in the Names Window ^^ above, you can search for the api without scrolling by simply typing it in, in this case I typed the whole name, but usually you only need to type “mes” and it will bring you close to your desired location. So now right click on MessageBoxA and click on “Set Breakpoint on every Reference”, this is in my opinion better then using the command line tool because if you use it and you type “bp MessageBoxA” and it breaks you will end up in a memory location and it just gets messy :/
So know we’ve set the breakpoints, minimize or close the names window, fire up the exe within olly, by Pressing F9, notepad should pop up, Try opening a file bigger then 32kb in notepad, bam it should of broke at this location:
00402D53 |. 6A 24 PUSH 24 ; /Style = MB_YESNO|MB_ICONQUESTION|MB_APPLMODAL
00402D55 |. 8B75 08 MOV ESI,DWORD PTR SS:[EBP+8] ; |
00402D58 |. 6A 00 PUSH 0 ; |Title = NULL
00402D5A |. FF35 B0604000 PUSH DWORD PTR DS:[4060B0] ; |Text = "This file is too large for Notepad to open...
00402D60 |. 56 PUSH ESI ; |hOwner
00402D61 |. FF15 30744000 CALL DWORD PTR DS:[<&USER32.MessageBoxA>>; \MessageBoxA ß need to get rid of this call
00402D67 |. 83F8 06 CMP EAX,6 ß Clicked NO?
00402D6A |. 0F85 A9000000 JNZ _NOTEPAD.00402E19
00402D70 |. 68 04010000 PUSH 104 ; /Count = 104 (260.)
As you can see it calls MessageBoxA, if user presses Yes it opens up wordpad, If user clicks No It jumps past the code that opens up wordpad and processes your file. So we can do this the quick and easy way, which is making the first instruction.00402D53 |. 6A 24 PUSH 24
Which is 4 bytes a “jmp short 00402D70“ which is perfectly 4 bytes ..
Why do we do this? Because it will jump straight past the messagebox and the jnz, straight into the first instruction after the jnz, which processes the code to open up wordpad.
Ok so in olly, click on the Push 24 instruction, press SpaceBar Which allows you to assemble instructions, type “jmp short 00402D70”, click ok, try to open a file bigger then 32kb again, boom it works. Ok in olly press ctrl+f2, it might say some error about corrupted breakpoints, whatever…
Pres Ctrl+G to goto a specific code location, type 00402D53 which is our location for Push 24,
Assemble the instruction in (jmp short 00402D70)
Ok so now we know where our Location of code that needs patching is, and the bytes we need to use to patch the exe:
00402D53
EB 1B = JMP SHORT _NOTEPAD.00402D70
COOL NOW THE FUN PART LADIES AND GENTLEMEN, SEEMS THAT THIS TUTORIAL TURNED OUT TO BE SPECIFICALLY FOR NEWBIES ON HOW TO PATCH NOTEPAD THE GOOD WAY. Just Kidding..
Well not anymore, This is the Part about Inlining, Finally!
Ok Have we all read Mr_Geek’s Tute? If not do so, it’ll make this part easier..
Assuming you’ve read it:
Ok open up the packed exe (the original one) in olly debug, it’ll say something about its compressed, and asking if you want to analyze the code, say no, if you press yes it can lead to bad packer code, if you pressed yes by accident, you can delete the notepad.udd file in your olly dir, then restart olly and load the file up again.
Ok so we’re in the code:
And we see this
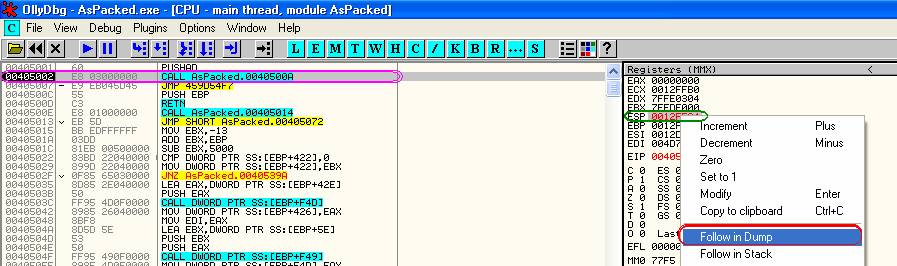
0040C001 > 60 PUSHAD
0040C002 E8 03000000 CALL NOTEPAD.0040C00A
So we press f8 once to trace over the first instruction, and we are on the first call, look over into the REGISTERS (FPU) window, and you will see the value ESP is RED, then we right click on esp, and goto “follow in dump",
highlight the first 4 bytes:
In yours it might be different. I really suggest you read Mr_Geek’s tute if you get lost in this part, its simple and small tute only take 10 mins to read. Get it from: http://biw.rult.at/tuts/mupaspack.rar
Ok so,
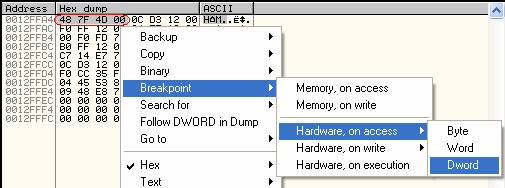
We Right Click and goto breakpoint->hardware on access->Dword.
We then press F9 to run the app and wallah we break at the place where we need to be:
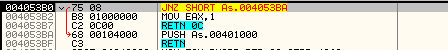
0040C3B0 /75 08 JNZ SHORT NOTEPAD.0040C3BA <-- We will be using this to jump to a CODE CAVE
0040C3B2 |B8 01000000 MOV EAX,1
0040C3B7 |C2 0C00 RETN 0C
0040C3BA \68 00104000 PUSH NOTEPAD.00401000 Push Address of OEP
0040C3BF C3 RETN (Used as a jump to OEP)
Ok so what we need to do is find a code cave full of nops or Null bytes... Packers tend to contain lots of Null bytes !
Ok so we scroll down for like 1 minute or so until we see lots of 00’s:
0040C59B 0000 ADD BYTE PTR DS:[EAX],AL
0040C59D 0000 ADD BYTE PTR DS:[EAX],AL
0040C59F 0000 ADD BYTE PTR DS:[EAX],AL
0040C5A1 0000 ADD BYTE PTR DS:[EAX],AL
0040C5A3 0000 ADD BYTE PTR DS:[EAX],AL
Ok let me explain a little what we are going to do now:
We’re going to change the JNZ which always jumps to the PUSH OEP, to jump to the CODE CAVE, Execute some instructions which will overwrite the bytes that we want to patch with our bytes (EB1B), then we assemble the PUSH OEP, RETN…
Ok so what we need to do is copy that location down: 0040C59B (the first address of the code cave) And change the
JNZ: 0040C3B0 /75 08 JNZ SHORT NOTEPAD.0040C3BA
To a JMP LONG 0040C59B so that right before it goes to the OEP, after its completed all of the decompression/decrypting, it jumps to a code cave, does some other stuff that we want it to do (in this case, overwrite some bytes with the MOV function) then jumps to the oep by reinserting the code into the code cave
The PUSH OEP, RETN which is:
0040C3BA 68 00104000 PUSH NOTEPAD.00401000
0040C3BF C3 RETN
Ok so we’ve made it so it jumps to a code location, now press f8 once, and it SHOULD land where the CODE CAVE is because remember it broke on the JNZ, and we changed it to a JMP to the code cave :P .. (oh by the way, don’t worry bout the instructions under the JNZ that get nopped because of extra bytes used when making a short jump into a long jump, them instructions aren’t used AT all so its unimportant to give a flying fux0r about em)
NOW PEOPLE. PAY ATTENTION:
We are now going to use the MOV instruction to do our work
We Remember the Location We Wanted to patch right? Yes it was: 00402D53
And We Remember Exactly What bytes we needed to change the original bytes to? Yes it was: EB1B
Ok so now let me explain what we are going to do.
In Olly, you should be on the first 00 in the code cave…
Press spacebar to assemble some instructions.
Now because we need to overwrite a certain addresses bytes, we use the mov instruction in the form:
MOV BYTE PTR DS:[004xxx], bb
MOV WORD PTR DS:[004xxx], bbbb
MOV DWORD PTR DS:[004xxx], bbbb bbbb
What does this all mean? Well it overwrites the byte(s) in the address provided in the [004xxxx]
[Btw PTR=Pointer DS=Data Segment (if you were curious)]
By either doing it 1 byte at a time, 2 bytes at a time or 4 bytes at a time:
1=byte
2=word ß We gonna use this one
4=dword ß double word
(TIP: If the byte starts with a letter, eg. EB, then make sure it begins with a 0, Ex: 0EB)
Ok there 2 ways we can do it, with either using MOV BYTE PTR DS:[004xxx], bb twice (where 004xxxx = the address we want to patch, and bb = the byte(s) we want to overwrite it with, in this case EB1B), OR MOV WORD PTR DS:[004xxx], bbbb
Now if you want to use the 2nd one, then you must be aware that the bytes must be put in reverse, because it overwrites it in reverse if using the WORD or DWORD function.
Ok so We assemble this instruction in:
MOV WORD PTR DS:[00402D53], 1BEB
If you don’t understand what I’ve done here, then read up and come back to it, :/ sorry but I can’t do much more explaining, coz I’ll just be repeating myself, and that’s very inefficient! ;)
Ok but that’s not all! We still gotta do 2 more things!
PUSH THE OEP’S REAL VIRTUAL ADDRESS
RETN
Ok so assemble 2 more instructions in:
PUSH 00401000
RETN
After doing all this, your code should look like this:
0040C59B 66:C705 532D400>MOV WORD PTR DS:[402D53],1BEB mov instruction to overwrite bytes
0040C5A4 68 00104000 PUSH NOTEPAD.00401000 push oep
0040C5A9 C3 RETN Return to OEP (retn used as jump to oep)IF it does, SWEET, if you have done everything correctly as I said then it should work like a charm.
SO to complete this patch, don’t press any buttons especially F9…
Right Click on the code in the CPU window, goto Copy to Executable->All Modifications
A window should pop up, Click COPY ALL, Then another window should pop up with some code, right-click again and goto Save File, then select a place to save the file, and choose a file name..
IF THIS DON’T WORK, WHERE IN MY CASE IT DOESN’T READ THIS INSTEAD!!!
Ok this is a little trickier but it works :/, first click on the first patch we made (the mov)
Then hold down shit and click on the last patch we made (the retn), the right click, goto
Copy to Executable->Selection then right-click goto Save File, then select a place to save the file, and choose a file name..
BUT WAIIIT we haven’t finished that patch yet !! we still need to change the jnz to a JMP LONG 0040C59B because in this case we only saved those three instructions to the new file, we still need to change the jnz
So open up that file you just saved in olly, press ctrl+g and type in the address of the jnz (u should make note of it.. it was @ 0040C3B0 ), then press space bar to assemble an instruction, type JMP LONG 0040C59B ,
click on the first patch we made (the JMP)
Then hold down shift and click on the last patch we made (the nop), the right click, go to
Copy to Executable->Selection then right-click go to Save File, then select a place to save the file, and choose a file name..
So you should have highlighted these three lines this time
0040C3B0 /E9 E6010000 JMP NOTEPAD.0040C59B
0040C3B5 |90 NOP
0040C3B6 |90 NOPAlternatively you can do this the opposite way around which I just recently noticed (coz im updating this right now) is kinda easier… just make that location of the JNZ a JMP 0040C59B then highlight the code (jmp, nop, nop) Copy to Executable->Selection then right-click go to Save File, then select a place to save the file, and choose a file name.. Then Load that semi-patched exe into olly, do the same thing to get to the oep, then IT Might stuff up, but restart olly if it does, usually works… when you get to the jmp, trace over it, then put ur MOV patch and the PUSH OEP, RETN ... this is just one way, someone also suggested that instead of making the jnz a jmp, just change the push oep to push (address of code cave) … however I tried this and it kinda failed… anyway just experiment like I did.. I also decided to include a inline patched exe just to prove that it does work and that you must be careful … that’s the trick to it :P …
THAT’S IT!
Run the baby see if she works, yup she does, well over here anyways...
Now you can make a patcher for it that’s like 5kb ...
GREETS:
ALL CRACKING CHANNELS ON iRC!, BiW Team, RET, [everyone in there too many people to name] Feisu, MEPH, Oloron, Mr_Geek all other people who have helped along the way, Everyone I’ve forgotton I’m SORRY! .. I've decided i don't want too many personal greets coz i always forget some1 :~(
Some Screen Shots Stolen from MR_GEEK’s tutorial hope you don’t mind :P
Brought to You by: