|
Finding Correct Serials Author: Volatility Please Read The Disclaimer
Before Continuing.
I believe the serial number for this program is machine dependant, therefore the ultimate end goal would be to write a key generator. Let me know if you do! Prepare To Crack: Upon running the program,
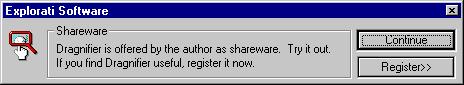
you're confronted with the following screen:
If you click the "Register>>" button, the screen will drop down, allowing you to enter a serial number. You'll notice that there is a code already there, your "Demo License Code" (you'll see later on that this is actually part of the serial number). Making The Crack: To see if we can trap our valid serial number, enter a dummy code into the text box (or leave the demo code). Now we need to find the breakpoint to set in Soft-Ice to trap the serial number. The most common breakpoints in 32-bit Windoze programs are GetWindowTextA, and GetDlgItemTextA. To save you time, the one we need is GetWindowTextA. With your dummy code entered,
press Cntrl+D to enter Soft-Ice. Set a breakpoint on GetWindowTextA
(BPX GETWINDOWTEXTA). Press Cntrl+D or X to exit back to the program.
Press Enter, and Soft-Ice will pop up. Press F11 once to get out
of the code, and you should be here:
Normally, we would have to step through the code for a bit, to find the location where our serial number is compared... but in this case, the entire routine we need is right here. All you need to do is step through the line "CALL 5F4028BB", and display the ECX register, by typing: d ecx. Now you'll see the code you entered, followed by some characters from the original "Demo code". Scroll down just a little bit (Alt+Down Arrow), and you'll see the original "Demo Code". Scroll down just a bit more, and you'll see another code. What's this? My "Demo Code" was A-386F15DD-D1FA, and the new code was AF48-8FF29E0D. After writing this number down, I exited Soft-Ice, and tried it. Hmm... didn't work. So I redid the process again, and found the answer. If you keep scrolling a bit more, after the first occurances of the codes, you'll see that the new code is appended to the original one. So the correct registration code was: A-386F15DD-D1FA-AF48-8FF29E0D.
Copyright © 1999 Volatility And The Immortal Descendants. All Rights Reserved. |