|
Finding Correct Serial Numbers Author: Volatility Please Read The Disclaimer
Before Continuing.
The programs I've cracked here so far, all work with this method, so I'm assuming they all will. Gregory Braun puts out some damn good, useful and innovative software, so please pay for these programs. Don't be a lamer and use my registration info either. All the programs I've
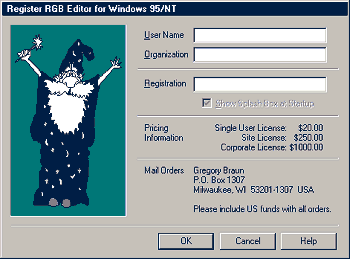
seen have a registration screen that looks like this:
So, we have a User Name, Organization, and Serial Number to enter. Judging by this, we could get more easily lost trying to patch, than we could just hunting for a correct serial number. The program we'll use for this example is "RGB Editor". The first method I tried for this target was the HmemCpy function in Soft-Ice, and it works just fine. So, Type some dummy data into the text boxes (Cracked by Volatility [ID], Immortal Descendants and 272727 for mine). Making The Crack: With your dummy data entered, press Cntrl+D to enter Soft-Ice. Set a breakpoint on HmemCpy (BPX HMEMCPY). Press Cntrl+D or X to exit back to the program, and click "OK". Soft-Ice will pop up. Now, we could step through the code, but if we think about it, the procedure will be called THREE times... once for your user name, once for your organization, and a final time for the serial number. So, press Cntrl+D two times, so that we're at the third occurence. Press F11 once to exit
the code, and you should be here:
If you look on the line above the command window, you'll see "USER(0A)". This isn't where we need to be, so step through the code using F10, until you see "RGB!.text" on the line... now we're in the program code. Step through the code
several more times to look for the place where our serial number is
calculated. You'll find it here:
We can display our organization by stepping through the line "PUSH EBX", and typing d ebx. We can display our user name by stepping through the line "PUSH ESI", and typing d esi. But now how do we display our serial number? We don't really... if we step through the line "CALL 00409520", we can get the value of EAX by typing ? eax. There's your serial number! Mine was 3727125845 .
Copyright © 1999 Volatility And The Immortal Descendants. All Rights Reserved. |