| Program Name: |
Shadows Of The Empire 
|
| Date: |
22 - Oct - 1999 |
| Objective: |
Run Without CD |
Heya i've got nothing to do so i'll write this tut for
removing the CD check on S.O.T.E
- There are a few types
of CD protections around, some hardcore
- some not, this happens
to be a simple check. Most commercial
- software will allow you
to install the whole game to
- your harddrive and let
you run it from there, but they usally
- always ask for the CD,
this is so you don't go installing on your
- mates computer, i find
this annoying so i remove the check
- for my own purpose
anyway.
-
- Ok install the game
with its maxium install option and wait about
- 20 mins if you have a
4x CD-ROM drive like me but i doubt you do ;),
- anyways once the
installation has finished remove your CD and place
- it on the floor or when
ever you store your CDs. Now run the program
- and you will see this
message.
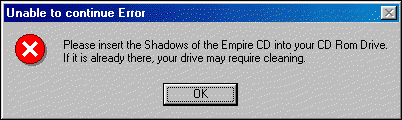
- Ok this time set a
breakpoint on messageboxa like so- Ctrl+D to activate
- SoftICE then type BPX
MESSAGEBOXA now exit SoftICE, rerun the program,
- SoftICE will break just
before the messagebox now press F12 to return to
- the line after the API
was called in the main exe code.
-
- There are several ways
to beat a standard check, you could trace on from
- the message box until
you hit a RET and find the CD check call or you
- could use wd32asm to
find where the msg box was called from a change
- a jump.
- K, we'll just use
SoftICE. anyway once you have returned from that API
- you will see the
following code :-
-
- 00463D1F CALL
[USER32!MessageBoxA]
- 00463D25 Push 01 <-- We are
here
- 00463D27 CALL 004AA560
- 00463D2C ADD ESP,04
- 00463D2F POP EDI
- 00463D30 POP ESI
- 00463D31 RET
- The theory is that we
keep tracing(F10) until we hit a ret and are
- returned to a line
below a CALL,.. the CD-Check call, some times
- this can be toally
noped out or a jump above will determine to jump
- it or not, blah blah
- So lets keep tracing
until we hit the RET....dum de dum da dum de dum
- hey! when we hit the
CALL 004AA560 the program ends :P , hum looks
- like the program has
called a exit procedure to stop the rest of the
- code carrying on :P. ok
lets rerun the program and when we get to the
- call line, so that our
little grey bar thing is over 00463D27 CALL 004AA560
- lets try and skip this
line...what ya mean how? :P well if you look at the
- top right of the
SoftICE screen its says EIP=00463D27 this is the next
line
- to execute..our exit
call =:0->-< , so click up there and change it to
- EIP=00463D2C, or if
your unprivenged and have no working mouse or think
- having a mouse is
stupid in SoftICE you will have to type R EIP then
- enter the number,
anyway press F5 to exit SoftICE, and wang bang lalal
- the game runs!
-
- Ok now its time to
patch the game, so how would we go about doing this?
- well we could nop out
that Call 004AA560 which calls the exit routine,
- but naw that would be
stupid because it would call a error msg box then
- run the game, so lets
trace out the call and see what we can see :),
- So when you get to that
call that exits, um.. Call 004AA560, set the EIP
- to jump over it like
before and keeping tracing(F10) until we hit the RET
- and return from the 'CD
Check' call, now you should see.
-
- 0048FF09 CALL 00463C70
- 0048FF0E XOR EDI,EDI <- We are
here
- 0048FF10 CALL
[008C44C4]
- 0048FF16 CMP EDI,EAX
-
- Now you can see we have
returned from the call above which was the 'CD check
- error you haven't the
cd thingy' so now we can simply nop out that call, OR!
- or? or scroll up abit,
make sure your not half through typing anything then
- click in the code
window and scroll up a few lines, or press Pgup/PgDwn
then
- go setup your mouse for
SI ;), anyway now you will see:-
- 0048FEF5 JNZ 0048FF0E <- Hey a
Jump to ----
- 0048FEF7 PUSH 0073B5A8
- 0048FEFC PUSH 006F35A0
- 0048FF01 CALL 004AA350
- 0048FF06 ADD ESP,08
- 0048FF09 CALL 00463C70
- 0048FF0E XOR EDI,EDI <- We are
here / -----
- 0048FF10 CALL
[008C44C4]
- 0048FF16 CMP EDI,EAX
-
- Now can you see two
ways to kill the check?, well we know that if CALL 463C70
- is executed then we get
a NO CD error and exit, so we can either NOP out that
- call or we can change
the JNZ 0048FF0E to JMP 0048FF0E , because that will jump
- straight over the nasty
call, hmm about time i brought this tut to an end, its
- too big ;), SOOoo lets
patch that JNZ because its quick for me :P, we need
- the file offset so use
a program like ICZ's Adress->file offset thing from
- www.crackstore.com or search for the bytes in a
hex ed, make sure you have
- CODE ON in SI to view
the bytes, i'm just gonna search for em, its
- 0048FEF5 7517 ......JNZ
0048FF0E <- Hey a Jump to ----
- 0048FEF7 68A8B57300
PUSH 0073B5A8
-
- so with a hex ed search
for '751768A8', oh yer i forgot to mention
- which file :P, hehe, um
its not SOTE.exe you know why? good i'm off then,
- i mean, go back into
SoftICE to the JNZ and you will see in the SoftICE window
- -------------------SHADOWS!.text+0008EEF3-------------------
- which means we are
debugging in a file called Shadows, could be an EXE or
- DLL, so do a search in
your SOTE directory for a file called SHADOWS, right
- theres a doc file and
some other stuff but its mostly like to be the
- x:\xxxx\Sdata\Shadows.exe so go into your sdata dir
and patch the shadows file
- search for '751768A8'
and change it to EB17 we search for more than 7517
because
- theres mostly likely to
be more than one of em, anyway 75 which is JNZ to EB
- which is JMP and its
done, lalal trlal dum de dum and save, click, run, play
- laterz peepz.
-
-

