|
Finding Correct Serial Numbers Author: Volatility Please Read The Disclaimer
Before Continuing.
Well, my main motivation for cracking this program was due to the fact that lamers are requesting cracks for it CONSTANTLY in forums and on USENET, which led me to believe that there aren't many cracks for it on the net Finding the correct serial number for the user name you enter isn't extremely difficult, but the method we use to "trap" it is kind of interesting. Prepare To Crack: If you're running WinAmp
for the first time, the nag/help/info screen will pop up, otherwise
you can access it by right clicking on the WinAmp title bar, and choosing
"Winamp", then click the "Shareware" tab. When you click
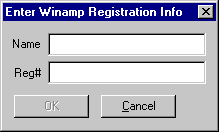
on the "Enter Registration Info" button, you'll see the following screen:
Notice that the "Ok" button is disabled. We need to enter the correct serial number before we can click "Ok"... bummer! Now we can't set up a breakpoint in Soft-Ice to make it pop up when the function is called... or can we? Make sure you're still at the registration screen, and press Cntrl+D to enter Soft-Ice. Set up a breakpoint on HMEMCPY (BPX HMEMCPY), then press Cntrl+D again to exit back to the program. Now try to type in some test data... at your first character, Soft-Ice pops up. With this information, we now know we may be able to trap the valid serial number anyway, we just have to find the correct function, as HMEMCPY is too general, and you have to know exactly where to look. Two of the most common functions we can use to narrow our code down are "GetWindowTextA" and "GetDlgItemTextA". To save you time, the function that we need is GetDlgItemTextA. Making The Crack: Enter some test data in the registration screen (Cracked By Volatility [ID] and 272727 for mine), and Press Cntrl+D to get into Soft-Ice. Set a breakpoint on GetDlgItemTextA (BPX GETDLGITEMTEXTA) and press Cntrl+D again to exit back to the program. Since we can't press the "Ok" button, let's try something different. Delete the last character of your serial number... NOT your user name. Soft-Ice will pop up,
and you should be here:
Now we need to look for
the place where our serial number is compared with the correct one,
which will normally be in the form of a CMP or TEST, and usually
followed by a jump. Step through the code by pressing F10, and
this is where we need to be:
The line "PUSH EAX" is where the serial number we entered is stored... if you step through this line to execute it, so that the line "CALL 004261E0" is highlighted, you can view your serial number by displaying eax (d EAX). You may have to scroll up a bit using the Alt+Up Arrow keys. Now we know the serial number is stored in EAX... what do we think the line "CALL 004261E0" is? The function to compare your serial number with the correct one is being called. So, press F10 once more to execute this line. Now we should be able to view our correct serial number by displaying EAX again (d EAX). Hmm.... nothing... looks like it's encrypted. My intuition tells me this is where we need to be to get our correct serial number though. Let's get the value of EAX by typing: ? EAX. Write this number down. Mine was 52931318. After testing a little
more, and writing down a few more numbers (it's always a good idea to
check a little further, sometimes you're pleasantly surprised), clear
your breakpoint (BC *), and press Cntrl+D to exit to the program.
Leave your user name the same, and the value you wrote down for the
serial number. To our surprise (well, maybe we aren't THAT surprised
:) ), when we type in the last character, the "Ok" button is now enabled!
Job done.
Copyright © 1998 Volatility And The Immortal Descendants. All Rights Reserved. |