Research Trends in Information Assurance and Network Defense in the Global Environment
Dr. Bruce C. Gabrielson, NCE
Christopher M. Pohl, CISSP
Mr. James M. Wilson
Booz Allen Hamilton Inc.
900 Elkridge Landing Road
Linthicum, Maryland 21090
Abstract:
Every day new ways are discovered to attack, control, disable, disrupt, and change digital information. Protecting critical information technology assets from attacks has become a priority for governments, industries, and individuals that use interconnected networks. The challenge includes not only maintaining productive operations, but also securing physical assets content, and intellectual property. Yet, current information assurance and network defense practices are sometimes primitive adventures in the manual monitoring of computer displays, reading bulletins, and interpreting log files. This often tedious process limits the effectiveness of protective and responsive measures.
For protection or responses to be effective, emerging networks need to be viewed as sophisticated self-aware organisms, able to see threats before being compromised, able to learn from data correlation, able to continuously map users and resources and able to be continuously aware of “social interaction” among hosts and devices. These “intelligent” networks function as organic mechanisms with sensors, monitors, and other tools that inform and protect. This paper explores how U.S. organizations approach emerging research focus areas and techniques employing the “network organism” paradigm. Our methods are aimed at solving pressing assurance and defense issues in the enterprise environment of the future.
Introduction
Information technology has become a vital component in the success of any activity or organization. In the United States, Information Assurance (IA) is defined as the practice of protecting and defending information and information systems by ensuring their availability, integrity, authentication, confidentiality and non-repudiation. This also includes disaster recovery and continuity of operations. To survive and be successful, an enterprise must have a disaster recovery strategy and response plan in place to mitigate the effects of natural disasters (e.g., floods, fires, tornadoes, etc.), inadvertent actions by trusted insiders, terrorist attacks, vandalism, and criminal activity.
The focus on IA now has a network-centric component. In addressing Defense-in-Depth, we have moved away from systems and platforms and our focus is now more on the network. IA is still a major concern, but computer network defense (CND) has become an important part of an IA layered defense.
CND includes:
- Situational Awareness
- Situational Understanding
- Decisive Response
This continuum includes the following capabilities.
- Deterrence
- Monitoring – Analysis – Detection
- Appropriate Response
Technology professionals have realized this new focus and have adjusted their thinking about
protection needs. These IA/CND professionals now share four common challenges in protecting and
defending their assets.
- 1. Design systems to protect data as it is created, stored, modified, displayed, moved, processed, and disposed of
- 2. Provide assurance and control capabilities in a “common operational picture” among decision makers and responsible parties
- 3. Recognize and react to threats and vulnerabilities
- 4. Sustain a knowledgeable and empowered workforce.
The objective is to safeguard information and computing assets, locally or globally, from conditions that might interfere with, or compromise their intended use. As technology makes quantum advances, it is ever more difficult to address and solve security problems “after the fact”. Adding security to an existing design is an increasingly ineffective approach. The challenge is to identify security solutions for the “most pressing needs” in assurance and network defense simultaneously with the system design. Even then, many technical “canyons” remain that cannot be addressed with current technology.
Background—A Historical Perspective
As few as ten years ago, most protected networks in both the private sector and government were in isolated enclaves. Network owners and administrators knew what and who was connected to their network, and employed the traditional network security controls needed to protect their assets. The external “curious browser” did not have sophisticated hacking tools and simply could not afford to do what is possible today. While these networks were expensive to establish and maintain, information assurance features (i.e., confidentiality, integrity, availability, and non-repudiation) were not considered as important to both governments and industry as they are today.
Because of their geographic dispersal and sensitive operating environment, government, military and intelligence systems were exceptions to the model. Most major governments employed some form of encryption to protect the confidentiality of their data as it traveled over public common carrier networks. Physical access controls (e.g., locks, fences, guards, etc.) were also used in these environments. In addition, only limited amounts of information were stored in widely accessible computers. Even in these cases, paper documents with the same data generally existed elsewhere within the enterprise. Data stored in computers were considered a supplement rather than a substitute for business records. The accompanying risk was primarily related to convenience of access rather than loss of access to vital information.
Today connectivity is the norm. Why would anyone buy a computer that cannot be immediately connected to a network? Internet access adds value to an otherwise expensive calculator or text editor. Robert Metcalf (the inventor of the Ethernet protocol) formulated the Law of Telecosm that says the value of a network is the square of the number of its interconnections. The potential value of a network exponentially increases as the number of connections increase. What was once mere software and hardware that had to be laboriously “configured” is now delivered as an interconnected and interdependent “solution.” Nor is connectivity limited to a physical wire. Wireless technology now provides “wire speed” connectivity.
Our information systems are no longer centered in easily bounded, easily protected isolated enclaves.
This leap from limited access to virtually universal entrée to unguarded systems has compounded risk
factors for government and commerce. Today, our CND and IA missions operate on a continuum designed to
provide an overall protection scheme throughout the global information grid.
Finding Our Problems
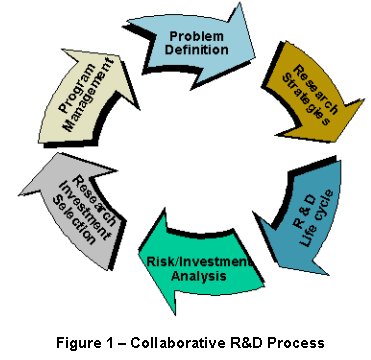 Figure 1 describes a coolaborative R&D process currently being implemented to identify, refine, and then solve CND research needs based on the collaborative environment we face today. Future advances in the science and practice of CND and IA are now, and will continue to be, supported through collaborative public and private sector research efforts. More than ever before, national governments rely on private sector companies and research institutions for intellectual and implementation expertise. Accordingly, private-public sector collaboration and cooperation is essential to advancing the art and practice of secure technology. Common ground between government and commercial standards also ensures mutual recognition of interests. One area where these interests converge is in conducting and exploiting research opportunities. However, with a general reluctance to share their information assurance and network defense problems, it has taken unprecedented cooperation among various organizations to identify
the many unsolved problem areas. Every organization has a few pet issues, but describing the specific problem and identifying the state-of-the art technology that might offer a solution has been both difficult and time consuming.
Figure 1 describes a coolaborative R&D process currently being implemented to identify, refine, and then solve CND research needs based on the collaborative environment we face today. Future advances in the science and practice of CND and IA are now, and will continue to be, supported through collaborative public and private sector research efforts. More than ever before, national governments rely on private sector companies and research institutions for intellectual and implementation expertise. Accordingly, private-public sector collaboration and cooperation is essential to advancing the art and practice of secure technology. Common ground between government and commercial standards also ensures mutual recognition of interests. One area where these interests converge is in conducting and exploiting research opportunities. However, with a general reluctance to share their information assurance and network defense problems, it has taken unprecedented cooperation among various organizations to identify
the many unsolved problem areas. Every organization has a few pet issues, but describing the specific problem and identifying the state-of-the art technology that might offer a solution has been both difficult and time consuming.
No single U.S. organization is responsible for all research initiatives. Nor is there any one laboratory, agency, or organization responsible for cyber security or cyber security research. Much of the U.S. research effort is concentrated in five federal agencies: the National Science Foundation, the National Institutes of Health, the Department of Energy, the Department of Defense, and the National Aeronautics and Space Administration. Activities that draw together top researchers from across the nation are sponsored by each of these organizations, or laboratories and agencies within these organizations, on a regular basis.
One popular method of identifying research needs and technology gaps within a particular organization is the community workshop. In this case, sponsoring organizations hold one or more workshops during the year where government, industry and academia are invited to participate in frank discussions on the related issues they have faced and the major issues they need resolved through research activities.
Information Assurance Technical Framework Forum (IATFF) conferences, sponsored by DoD and open to U.S. citizens only, are one of many community meetings that are held regularly to address a wide range of IA interest areas. These conferences are geared towards “professional networking” so are well attended by a broad group of stakeholders including both users and suppliers.
Another means of staying current on emerging IA needs is through annual DoD publications including agency research and technology forecasts and technical publications. DoD publishes a freely distributed updated version of the Information Assurance Technical Framework each year. This document was developed to help users both define and understand their technical needs as well as to select approaches to meet those needs. The intended audience includes system security engineers, customers, scientists, researchers, product and service vendors, standards bodies, and consortia. The objectives of the IATF include raising the awareness of IA technologies, presenting the IA needs of information system (IS) users, providing guidance for solving IA issues, and highlighting gaps between current IA capabilities and evolving needs.
How to Approach Research - A Model
From our workshops, conferences, and forums, each identified information protection issue is broken down into focused subsets, and themes emerge as to what technologies could potentially be applied to solve the problem components. Addressing larger IA and CND problems in terms of smaller components has helped us focus our research activities to achieve steady progress towards solving difficult overarching issues.
For each of the smaller problem subsets, business cases and selection criteria are developed to further focus our solicitation efforts in finding the correct entity to solve the problem. The case for commercial participation is broken down as follows:
- Identify technical components with commercial versus non-commercial applicability
- Assess development versus research focused elements
- Rough estimate of commercial and government market potential
- Evaluate funding and support requirements (rough evaluation)
- Level of investment funding required
- Timing of investment infusion
- Expected return.
Selection criteria for deciding on the organization with the best fit for the research effort is next developed. A typical set of guidelines for selecting a partner (broadly at the IA or CND need level) is as follows:
- Innovativeness of solution proposed
- Is it a comprehensive “organic” solution?
- Can it use existing technologies?
- Why it will be successful?
- Evidence of success
- Proof-of-Concept
- Definition of milestones
- Organization qualifications.
Prioritization of “What Do We Do First” - Risk Analysis
In case you are unfamiliar with risk analysis, it’s a technique whereby we can apply consistent
criteria against each risk element so the resultant values can be directly compared and prioritized
on an equal basis in terms of the risk each represents to a mission or operation. Then, depending on
the strengths and needs of the sponsoring organization soliciting the work, the potential for solving the
issue with existing technologies, and of course the budget actually available to spend on research and
development, these organizations prioritize the list of problem areas using risk analysis. From these
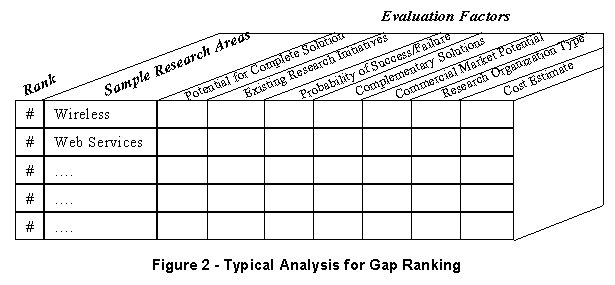
final prioritized lists, solicitations and announcements emerge. Figure 2 below represents a typical
example of how each potential research gap can be compared and prioritized.
Problems With the Model – Making Research Attractive
We have found that just identifying and defining the problem set is not enough to actively solve it. While government-funded laboratories will always be tasked to solve pressing problems, smart minds are not exclusive to these labs. Industry has tremendous resources, but industry will not be interested if there is not enough of a profit. Academia has tremendous, but limited, high-level resources, access to numerous low-cost student researchers, and the significant limitations with moving a potential solution to the development stage.
To “get the word out” and make research more attractive, U.S. Government organizations now use a wide range of methods to advertise and solicit research and development opportunities. The broad targeted audience includes private and public research laboratories, educational institutions, commercial organizations, small business, and independent vendors. The range of funding available also varies from small proof-of-concept seed efforts to major developments over a period of time. Current methods include:
-
1. Commerce Business Daily Announcements/Federal Business Opportunities (FedBizzOpps) Internet Portal
- 2. Department of Defense Small Business Innovation Research (SBIR) Program and the Small Business Technology Transfer (SBTT) Program
- 3. Agency Specific Programs (Normally advertised on the agency’s website.)
- 4. Unsolicited (White Paper) Proposals
- 5. Technology Investment Agreement (TIA)
The Federal Business Opportunities Internet Portal is identified as the single U.S. Government access port for identifying business opportunities exceeding $25,000 in value. The FedBizzOpps portal has replaced the Commerce Business Daily that previously served as the principal solicitation instrument for the Federal Government. The site primarily serves traditional vending arrangements with the Federal Government. While research solicitations can be found on the FedBizzOpps site, there are more targeted sites related to specific agency or departmental solicitations.
The Department of Defense has programs that target small businesses in an effort to harness the innovative capabilities of small technology companies. These include the SBIR and SBTT programs. These programs target research and development projects at small technology companies from proof of concept through prototype. The ultimate objective is for companies/projects to obtain funding from the private sector and/or non-government sources as products become viable in the private and/or public sector markets.
The purpose of SBIR is to create an effective vehicle for moving ideas to the market to benefit both private sector and public sector customers. The SBTT program funds cooperative R&D projects involving a small business and research institutions (i.e., university, federally-funded R&D center, or nonprofit research entities). Several other federal agencies have SBIR and SBTT programs that operate like the DoD model. Each agency program tends to focus on their individual mission requirements. Because all missions can involve heavy investment in information technology, nearly all these programs have information technology components.
Another typical approach is for agencies to use what are commonly called Broad Area Announcements (BAAs). The Defense Advanced Research Projects Agency (DARPA) uses BAAs to solicit proposals. DARPA is the central research and development organization for the U.S. DoD. The DARPA mission is to develop imaginative, innovative, and often high-risk research ideas offering a significant technological impact that will go well beyond the normal evolutionary developmental approaches; and, to pursue these ideas from the demonstration of technical feasibility through the development of prototype systems.
When traditional contracts, grant or cooperative agreements are not feasible, some agencies have the authority to enter into Technology Investment Agreement when in the public interest. Vendors and/or researchers also present unsolicited research or product ideas to federal agencies, usually in the form of white papers. Such proposals can result in direct awards or broader invitations/solicitations to the research community.
Technology-based economic development is also a priority for state and local governments as a means of strengthening community foundations. State and local governments make investments with industry and universities to develop work force skills to in an effort to become globally competitive. The Research Triangle Park in North Carolina has provided one of the original prototypes for this kind of regional economic transformation. In this case, the leaders of business, government, and universities have shown a sustained commitment to reaching a common goal.
The Research Triangle Park today occupies nearly 7,000 acres, and the research organizations housed there employ approximately 50,000 people. Businesses in fifty or so additional satellite research parks within a fifteen-mile radius employ an additional 70,000 people. Key elements within this contribution were made by the state of North Carolina, which invested in the educational infrastructure to include community colleges, technical training institutes, and support for the state universities.
A Sampling of Research Gaps
Current CND tools and technologies primarily consist of product-specific sensors that support network status displays and intrusion detection systems that aggregate data from varied sensors, monitors, and detectors. The tool outputs are then cognitively interpreted and translated into narrative constructs to provide decision makers with alerts and status reports. Often these status reports cover only local systems being monitored and do not indicate the operational impact from the statistics. Network owners and operators are increasingly overwhelmed with information from network security devices (e.g., firewalls, monitors, intrusion detectors, etc.) deployed on their networks. Distinguishing between routine, noise, and hostile network activity is increasingly complex.
Recent technical and functional advancement in CND tools focused on greater tool variety with larger data repositories and faster execution. Newer tools are able to collect data faster and in greater volume yet lack a corresponding increase in high-value analytical capability. Existing tool characteristics include:
- Massive data collection efforts
- Manual processing and evaluation of information
- Narrow view of local environment
- Manual configuration of individual devices and application.
Emerging enterprise level systems must have the ability to correct changes made by human administrators to minimize risks and threats. Both active and passive agents may be able to monitor, report, and take appropriate corrective actions without system administrative input. Decentralized access and control of information (i.e., knowledgeable repositories) is needed to track and monitor system daemons, devices, applications, and data throughout the network. Active and passive agents should be able to detect unidentified (i.e., possibly hostile) events based upon the policies and information threat models. These agents will have specific duties that are loosely controlled through combinations of software and hardware.
The malicious “insider” is a particularly vexing challenge to security. Research on insider threat mitigation will have a very high impact on the national security of any nation. The human characteristics of the insider and the nature of the insider’s motivations and goals are relevant to any solution to the problem. These individuals might compromise high-profile targets no matter what hurdles or barriers are in place. Defending against “social engineering” is a key weakness in many organizations. Correlating the intersection of psychosocial interactions among human actors, with network operations and management, to security policies, and minimization of data leakage into unwelcome hands is a difficult task. All of these elements affect how best to tackle the security threat as it relates to information systems security. If an attacker has a “key,” he doesn’t have to pick the lock.
Understanding the various threats and how the motivations of individuals who present these threats are just a small part of this “organic” research challenge. The complexity of monitoring and managing employees who are engaged with many different projects and the variations within the unique sets of data, including damaging, deliberate insider activity, is another challenge. The final challenge is identifying what potential solutions are currently available today, and what is being researched and developed that can be used in the near future. It is here the self-aware network would be particularly useful.
Wireless is another emerging technology where security risks are high and solutions are needed. Many countries have evolved towards a wireless community simply because of the practical limitations of not having cables available. Unfortunately, nodes in a wireless network are autonomous units and can be captured, compromised, and hijacked. Encryption and authentication can be used in a wireless network to reduce potential attacks, but they cannot eliminate the attacks if a node carrying the encryption keys has been compromised.
Making large amounts of information visually available and readily understood by humans impacts many related protection activities. Research is needed to improve the methods and techniques involving collection, aggregation, correlation, and visualization of information so decision makers can quickly assess their current conditions, predict future conditions based on evolving circumstances and make well grounded decisions. Current technologies do not operate at the enterprise level easily. As our collection and processing resources become faster and more complex, our ability to automate for better understanding must improve. We need to:
- Integrate network management and security functions and features more effectively
- Develop automated, yet flexible, correlation features
- Develop internal network intelligence and self-awareness to reduce operator information overload
- Create better decision aid tools (e.g., visualization, common analyst consoles)
- Incorporate automated policy enforcement mechanisms
- Create human-computer interface tools that assist in cognitive decision making
Conclusion
The traditional view of network management and network security as separate but equal functions has to be overcome. A number of IA and CND risks still challenge the research world. Security engineers need to the ability to quickly refine how their systems respond to new data, applications and/or network activities or incidents. These controls must contain automated capabilities to begin countermeasure procedures for any type of activity, threat, or condition faced by the organization’s communication channel or data processing capabilities.
Network technology is moving faster than those of us involved with the protection of information resources can keep up. We know our needs are often huge and that our final state-of-the art solutions must make use of commercial off-the-shelf products. Additionally, we know that with the speed of changes, U.S. organizations have been forced to find innovative methods to not only identify and describe our critical network defense and information assurance protection needs, but also have evolved a number of sophisticated marketing approaches for finding researchers with bright ideas for solving these needs. By packaging solicitations that offer rewards geared towards targeted markets, researchers can be selected from the proper mix of laboratories, academia, or industry resources. Combining all of these activities gives us a clearer picture of how to get where we want to go.
 Figure 1 describes a coolaborative R&D process currently being implemented to identify, refine, and then solve CND research needs based on the collaborative environment we face today. Future advances in the science and practice of CND and IA are now, and will continue to be, supported through collaborative public and private sector research efforts. More than ever before, national governments rely on private sector companies and research institutions for intellectual and implementation expertise. Accordingly, private-public sector collaboration and cooperation is essential to advancing the art and practice of secure technology. Common ground between government and commercial standards also ensures mutual recognition of interests. One area where these interests converge is in conducting and exploiting research opportunities. However, with a general reluctance to share their information assurance and network defense problems, it has taken unprecedented cooperation among various organizations to identify
the many unsolved problem areas. Every organization has a few pet issues, but describing the specific problem and identifying the state-of-the art technology that might offer a solution has been both difficult and time consuming.
Figure 1 describes a coolaborative R&D process currently being implemented to identify, refine, and then solve CND research needs based on the collaborative environment we face today. Future advances in the science and practice of CND and IA are now, and will continue to be, supported through collaborative public and private sector research efforts. More than ever before, national governments rely on private sector companies and research institutions for intellectual and implementation expertise. Accordingly, private-public sector collaboration and cooperation is essential to advancing the art and practice of secure technology. Common ground between government and commercial standards also ensures mutual recognition of interests. One area where these interests converge is in conducting and exploiting research opportunities. However, with a general reluctance to share their information assurance and network defense problems, it has taken unprecedented cooperation among various organizations to identify
the many unsolved problem areas. Every organization has a few pet issues, but describing the specific problem and identifying the state-of-the art technology that might offer a solution has been both difficult and time consuming.
