Written by: The Clone
Date: Tuesday October 19, 2004
Updated: Saturday, December 11, 2004
Web-Site: http://www.nettwerked.net
E-mail: theclone@hackcanada.com
Blending Hacking, Phreaking, Lock Picking, and Urban Exploration into one phile.
Dedicated to: Hack Canada and Nettwerked.
Representing the Canadian hack / phreak scene
for over 5 years, and to represent forevermore.
Written for: The Fall 2004 Issue of K-1ine Magazine.
Table of Contents:
- Introduction / Disclaimer
- Mircom System Features
- Exploiting Mircom Systems
- Conclusion to this Document
Introduction / Disclaimer:
This document is dedicated to subverting the physical and remote security of the Mircom Telephone Access System, supposedly "uncrackable" machines widely used across Canada / the United States. Mircom Technologies, the company that invented these bitches, manufactures a full range of other security products which include fire control and communication products dedicated to life safety in the telephone access markets.
In this document you will: learn what the Mircom Telephone Access Systems are, learn how to administrate the systems, and learn how to use a few "tricks" I have discovered in order to gain both building access, elevator control, free long distance telephone calls, and to cause general mayhem in your community.
Now this is your warning; none of the knowledge you pick up from this article should EVER be used in practice. Unauthorized access to the administration functions of a computer controlled system of any kind, including building security systems is against the law. This file was simply written as a resource for individuals who want to learn about the unknown such as what big business and government agencies wish to keep from the public. This file is written for people sick of ignorance. If you do not want to use this knowledge as anything but a resource for your criminal activities, I advise you to STOP reading. Hell, don't stop reading... I'm not responsible for your behavior and could really care less that you want to spend the rest of your life rotting in a prison.
Mircom System Features:
The Mircom Technology Building systems range in size, in cost, and of course in features. Since I didn't feel it absolutely necessary to list off every single feature of each model, I simply linked to their data sheet PDF files. Make use of the resources linked off the images. There's a lot to learn about the models that I could not have possibly put better myself.








|
Exploiting Mircom Systems:
Lets face it; every physical and remote computer controlled infrastructure on earth, whether it be some guy's personal computer or some lonely mainframe in a downtown office is vulnerable in one way or another. Don't be fooled by the marketing gimmicks being thrown your way by big business conglomerates out to make a buck on your ignorance. Every single Mircom Physical Security System around the planet is secured by a company that happened to have leaked it out to the wrong person. Now you're probably thinking to yourself "Yeah right, Clone. You're pulling my leg. You can't be telling me Mircom was that stupid!" Well they were. Now before you get too excited; I'm going to be straight with you; I will not be publishing the passwords. Don't bother asking me for the codes, because for all you know I don't even have them - and never have. But don't fret, my pet, I will let you in on a few interesting secrets anyways.
Physical Administration:
Mircom Technologies decided the best way to keep landlords and building owners from permanently getting locked out of administrating their security systems when they decide to forget their password, was to implement a 10 or 12 digit override password (factory default) that could work on every model. That way Joe Nobody has to pay Mircom a nice fat consulting fee every time he gets piss-drunk and loses the cigarette package he wrote the administration password on. The fucking hillbilly should have gotten the password tattooed on his ass.
For this particular article I will be using the Mircom TAS-2000 Telephone Access System (MUS-3140K) as Physical Administration "subject matter".
Now before you jump into finger hacking this system to death, you must, and I repeat must, *always* check for one of two things; people and cameras. People are less of a threat, because most of the time they will figure you're just calling someone you know in the building, and at times will even offer to let you in the building. External cameras watching the doorway and, depending on the model and the hardware implementation, a hidden camera (model #: CAM-1) located inside of the Mircom telephone access system itself may be watching your every move. If you notice a camera is possibly built into the model of Mircom you're about to hack, walk away. Come back a few days later and wear some kind of disguise; such as a head scarf that covers your entire face, or better yet a balaclava for a more phearsome "I'm gonna 0wn this b1tch!" look.
As you approach the Mircom Telephone Access System you will notice a screen (unless altered by the administrator) that says: "Mircom - Enter Dial Code"
|
Enter Dial Code [99__] |
(Don't worry the password is asterisked ************ for your "security".)
|
Enter the Password [__________] |
|
>Add new record Edit record |
You are now at the main menu. If you choose the "Add new record" option you will then have the ability to add extensions which dial any telephone number you want. If the building administrator did not set up a toll-block with the telecom carrier servicing the dedicated line, you can program long distance numbers including international and 1-900 pay telephone numbers into the system. So let's assume you have a need to enter into that menu, you will immediately be brought to this screen which says "Enter Dial Code [____]". At this point, dial any extension you want to program into the system for later use; such as 1234.
|
Enter Dial Code [1234] |
|
Enter Telephone No. [______________] |
|
Enter Elevator Code [__] |
|
Enter Elevator ID [__] |
|
Add new record >Edit record |
|
1114>_______________ 108 *************** |
|
Edit record >Delete Record |
|
_22 *************** 127>*************** |
|
Delete Record >Main Door DTMF |
|
Main Door DTMF [9] |
|
Main Door DTMF >Aux Door DTMF |
Online Timer programming
|
Aux Door DTMF >Online Timer |
|
Online Timer [0060] |
|
Enter new password XXCENSOREDXX |
|
[MM/DD/YYYY][HH:MM] [__/__/____][__:__] |
|
0554.08/28/04 04:00 Code:2600K Acc:Yes |
|
Date : 08/28/2004 Time : 04:01:09 |
|
Sort by name >Sort by dial code |
|
Auto Sort Order >Select Language |
The options: 0=E (English), 1=F (French), 2=S (Spanish), 3=M (Mandarin).
|
Enter Language [0] 0=E,1=F,2=S,3=M |
|
Select Language >Set NSL ID and SP |
|
Enter NSLA ID & SPA [_9][99] |
|
Enter NSLB ID & SPB [_9][99] |
|
Enter NSLE ID & SPE [23][33] |
|
Set NSL ID and SP >Set ELV ID and Time |
|
Enter default ElevID [__] |
|
Set ELV ID and Time >Auto Program |
|
Enter start dialcode [____] |
|
Auto Program >Set Tone/Pulse mode |
|
Select tone/pulse [0] [0=T,1=P] |
|
Set Tone/Pulse mode >Options |
|
Enter Option Code [0128] |
|
Options >Reset |
|
Are you sure! [*=Cancel] [#=Ok] |
|
>Initialize Logging Init/Erase all data |
|
>Init/Erase all data Exit |
|
Init/Erase all data >Exit |
Mircom Keyless Entry:
With a 4 digit keyless entry code, you have 10,000 possible combinations to try. When you enter the login ID (9998 or 0001) you will be asked for a pin code. When you get the pin code wrong, there will be a 3-5 second delay before you are brought back to the main menu which shows "Enter the dial code" on the screen. Try obvious combinations first: 0000, 1234, 2004, 9999, etc. If those don't work, work your way up; there is a high probability you will get the correct keyless entry code before trying all 10,000 combinations - unless of course the administrator didn't set a keyless entry code. Those silly bastards.
Other ways to open the door for keyless entry:
I've thought of two other ways to get access without physically breaking the door open or waiting for someone else to let you in. The first way: I noticed that in some cases misconfigured or inactive extensions for all of the Mircom Panel models will give you a 0+ operator. In my case Telus is the telco. If you social engineer a 0+ TOPS/TSPS operator into transferring you to a number (tell them your telephone keypad is jammed and it's urgent), such as a cell phone, you could then answer that cell phone and press '9'. The DTMF "9" key triggers the Mircom box which in turn opens the door when pressed. The other way to gain access for keyless entry is by blasting DTMF "9" into the voice mail message of your cell phone or landline beforehand and then when the time is right, social engineer a 0+ operator and have them transfer you to that telephone number. The problem with the second trick is that you might have problems with remote-controlled voice mail systems, such as most versions of Audix/Octel/Meridian Voice Mail System which stops recording when you hit any DTMF key on the telephone. Old-school tape recorders which allow you to record anything (including DTMF) will work fine enough indeed.
Even MORE ways to open the door for keyless entry:
(Added 12/11/04, suggested by CYB0RG/ASM)
Tried tested and true. This trick requires either a cell phone that can generate loud and accurate DTMF, or a tone dialer with a fresh set of batteries. In order to make this trick work, you have to call up any random extension available on the Telephone Access Panel. When the call rings through you may either press DTMF "9" before the call is completed, or after someone or something (voice mail) picks up. Be sure to place the cell phone or tone dialer against the speaker of the access panel for the best results. If the door opens, you will hear a short echo of the DTMF 9 emitting from the panel, then a short buzzing sound for up to 5 seconds. This means the door has opened!
A successful door entry hack is shown below in this photograph:
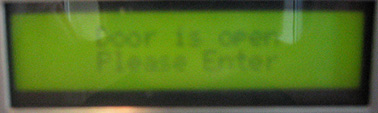
Conclusion to this Document:
This completes another article by yours truly. I expect this document opened up your eyes to another aspect of hacking and phreaking you might not have otherwise thought to research and exploit had you not sat down read this fine piece of modern literature. In conclusion to this article, I just want to say one thing; don't stop exploring. Don't stop your desire to explore beyond the boundaries set forth by the powers that be. Get out, play with technology and make it do something it wasn't intended to do. And don't ever stop sharing that knowledge with other like-minded individuals. Hackers and phreakers need to stick together like shit to stink! Peace.
.eof
This document is Copyright © 2004 by Nettwerked Incorporated. All Rights Reserved.